Technical cybersecurity
Technical cybersecurity
Related topics: Cybersecurity in information systems, Legal cybersecurity
The computer system represents a primary dimension of a public entity's or company's information system. In general, it can be thought of as composed of interconnected processing systems through electronic, computer, and telecommunications technologies to share resources and services.
The security of a company's computer network is an essential element in ensuring the full utilization of all sharing and communication services available.
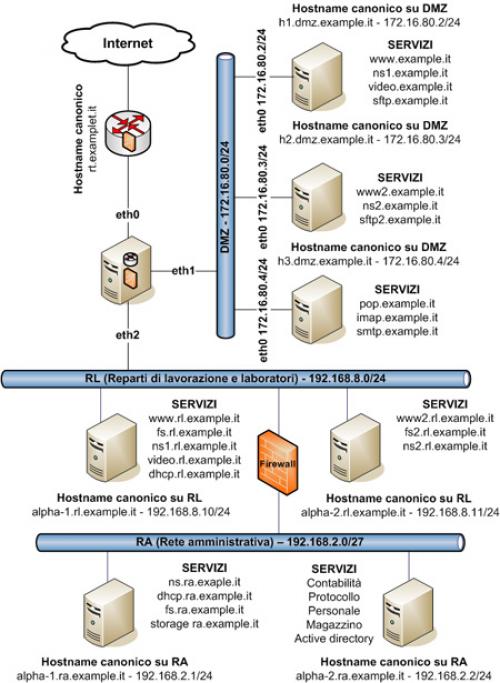
By way of example, the network architecture of a medium-sized company is shown, highlighting that network services are generally distributed across multiple segments.
In the area called the DMZ (Demilitarized Zone), the main network services accessible from both the internal network and the Internet are located: this is the only zone accessible from the Internet.
The operational departments and laboratories are located in the RL network segment, where the internal services necessary for the functioning of the production area are located.
Then there is the RA network segment - administrative network - with administrative management services, separated from the RL network by a firewall.
A bastion host, equipped with three network interfaces, implements the firewall and routing between the DMZ, the RL segment, and the Internet.
In rare occasions and with due caution, the use of tunnels and/or VPNs may be allowed to establish connections to internal segments.
It is evident, therefore, that monitoring network services in all zones is essential to:
- prevent DoS attacks (Denial of Service)
- prevent intrusions
- prevent theft of projects or documents
- prevent identity theft
- prevent DDoS attacks (Distributed Denial of Service), which involve using multiple computers in one's network to launch attacks against other networks considered more important by hackers
A Proactive Approach to System Security Can Lead to Success
Implementing Intrusion Detection Systems (IDS) to detect Trojan horses, backdoors, IP spoofing, session hijacking, and password cracking attempts is crucial.
To analyze the security of a system, system scanners and network scanners are used. System scanners are executed locally and are used to identify any weaknesses that would allow a local user to gain unauthorized privileges on insecure or outdated files or configurations.
Network scanners, on the other hand, are used to check for vulnerabilities accessible through the network. A network administrator should also run scan detectors because hackers also use scanners to gather information about the system.
Preventing Denial of Service (DoS) and other network attacks and configuring key network services such as DNS, FTP, WWW, and other daemons is essential to avoid potential paralysis of the company's network with difficult-to-quantify damages.
For this reason, alongside proactive security analysis tools, it is recommended to design, position, and test one or more secure firewalls.
Protection with Adequate Software Programs
The protection of individual machines on the network is equally important. Viruses, worms, keyloggers, phishing, rootkits, adware, botnets, etc., are vehicles of infection that operate, sometimes in combination, at multiple levels. Therefore, it is necessary to have a product that incorporates cooperating protection modules such as:
|
Cooperating Protection Modules
|
|
| File Antivirus |
Bidirectional Firewall |
| Mail Antivirus |
Intrusion Prevention |
| Web Antivirus |
Anti-spam |
| IM Antivirus |
Anti-phishing |
| Application Control |
Anti-banner |
| Proactive Defense |
|
