Wireless networks
Related topics: Networks
Wireless Networks
Why Have a WiFi Network?
The demand for mobile access to corporate networks and the Internet has become an essential requirement for many companies and institutions. Offices, laboratories, meeting rooms, and auditoriums can integrate the existing wired network with mobile access, allowing the connection of new generation hardware such as wireless printers and external hard drives.
The mobile connectivity service is used not only in regular work activities but also during conferences, meetings, and any situation where the audience wants to connect their portable devices to the Internet. This raises the need for careful analysis of coverage areas, as well as addressing security and integration aspects with existing networks.
Hotspot Networks
The term hotspot refers to an intranet accessed through an authentication page or a simple advertising page before being redirected to the initially requested pages.
Access to the hotspot area is managed through the mechanism of a Captive Portal, which can be accessed using both mobile devices and fixed workstations connected to the intranet with LAN cables. Initially, this mechanism requires self-registration, the process of which depends on the service provider. In most common cases, the username is either the mobile number or the email address, with a password chosen by the user or assigned by the system. In most cases, hotspots are of the wireless type.
With the increasing popularity of mobile devices, there has been a growing demand for hotspot areas. Airports, trains, hotels, restaurants, and bars have started to provide free or paid hotspot areas. Some municipalities in Italy have activated free Wi-Fi hotspots in squares and parks, allowing their citizens to browse the Internet or access online municipal services.
Hotspot networks also enable proximity marketing by sending users advertising messages through the Captive Portal during the registration or login phase. User profiling in Wi-Fi networks allows for the configuration of time-based profiles, traffic-based profiles, or a combination of both, where reaching one limit automatically becomes the operational limit. The configured profiles can be either free or paid.
Coverage Areas
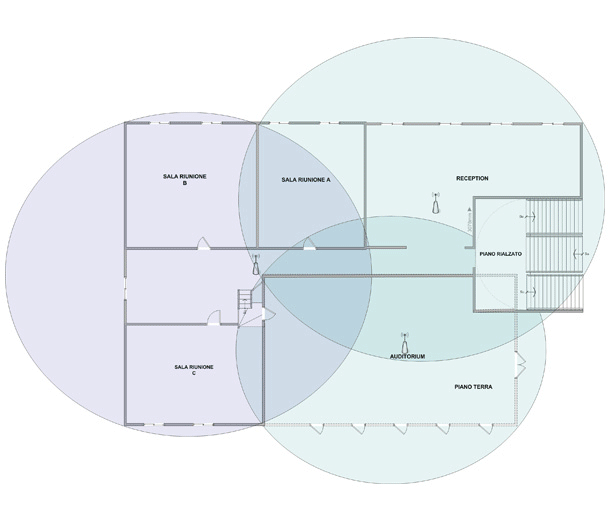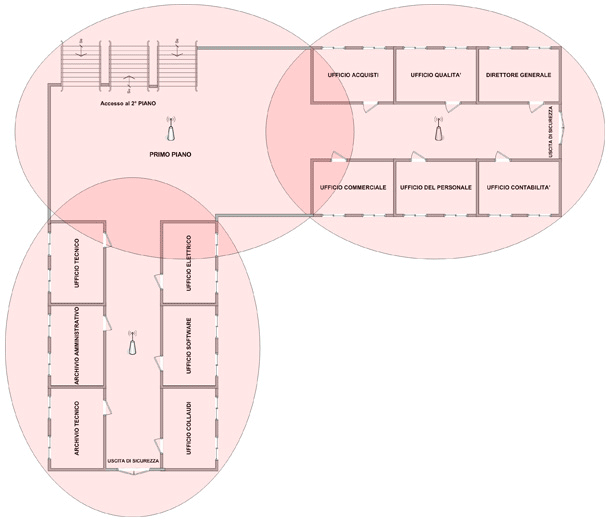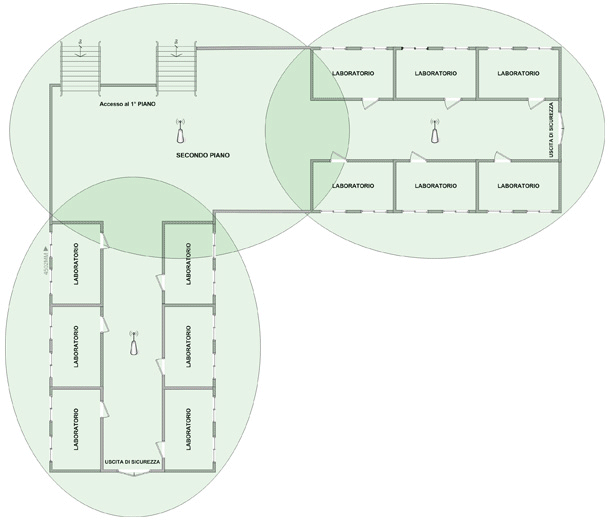
The optimal coverage of identified areas necessitates the analysis of physical factors that affect the maximum range of the radio signal from the employed WiFi devices, including transmitter power, number and positioning of antennas, and materials separating the transmitting system from the receiving system. In the absence of barriers and interference, the natural shape of coverage zones is spherical symmetry. However, the elongated shape of building floors and the arrangement of barriers often suggest ellipsoidal coverage zones that, when projected onto a plane, take the form of an ellipse.
It is evident, therefore, that the overlap of coverage zones with circles is only theoretical and not actual, as the presence of barriers degrades the signal quality of coverage.
Access Modes and Security Issues
There are different access modes to connect to a WiFi network. The most common situation is to allow sector-based access: each zone is controlled by a password and MAC address filtering to further enhance the level of security. Each network device is directly identified by the manufacturer with a unique 48-bit, 6-byte physical address. The physical address is often represented in hexadecimal format, such as F0:A6:15:1F:03:7E. By mapping the device's access to its MAC address, only the device listed in the authorized devices' list is granted access. This way, only the physical addresses that have been previously added to the list of authorized network devices and are therefore known can be enabled.
Content Request Filtering
The pairing of the physical address and the network device allows for the creation of a correspondence table capable of identifying the owner of the mobile device and the zone from which they are connected. Consequently, it is possible to apply MAC address-based filtering policies to allow or deny access to resources for the identified device. Device-based filtering can be performed based on a list of authorized requests or a list of denied permissions. These are commonly referred to as a whitelist and a blacklist, respectively. Additionally, the analysis of responses directed to devices can be subject to content filtering. Once implemented, this type of mechanism naturally raises issues related to individual freedoms and rights.
